205 words
1 minutes
某高考查大学专业网站
https://www.gaokao.cn/school/263/sturule
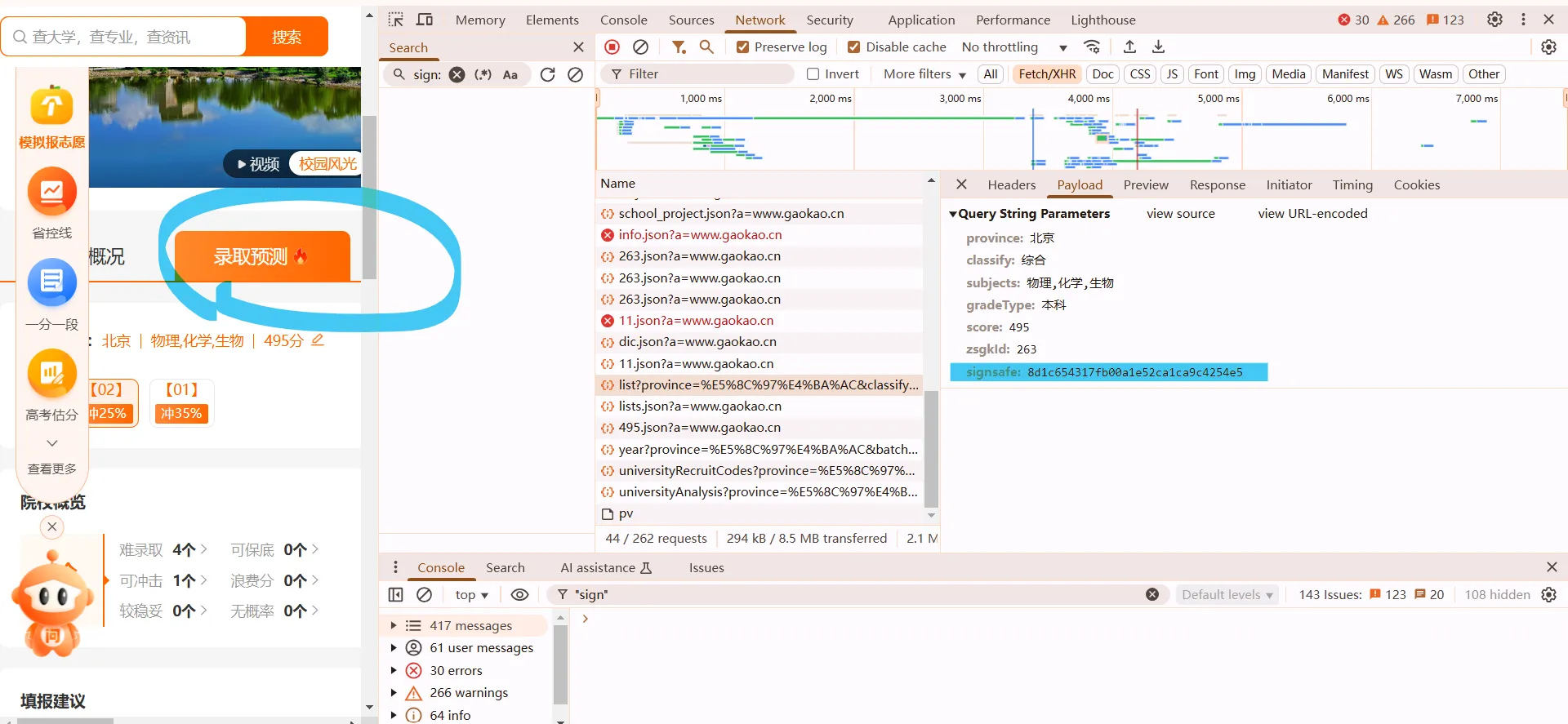
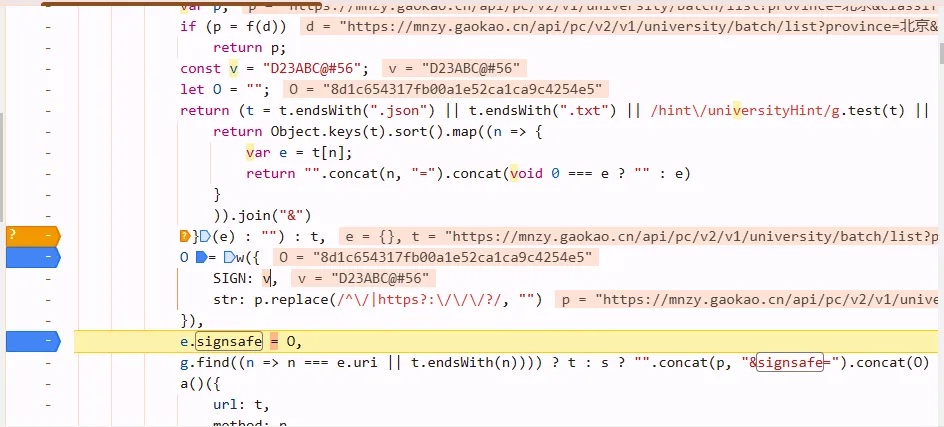
在此js文件内搜signsafe。随便打几个断点,发现t是url,可以利用它下条件断点
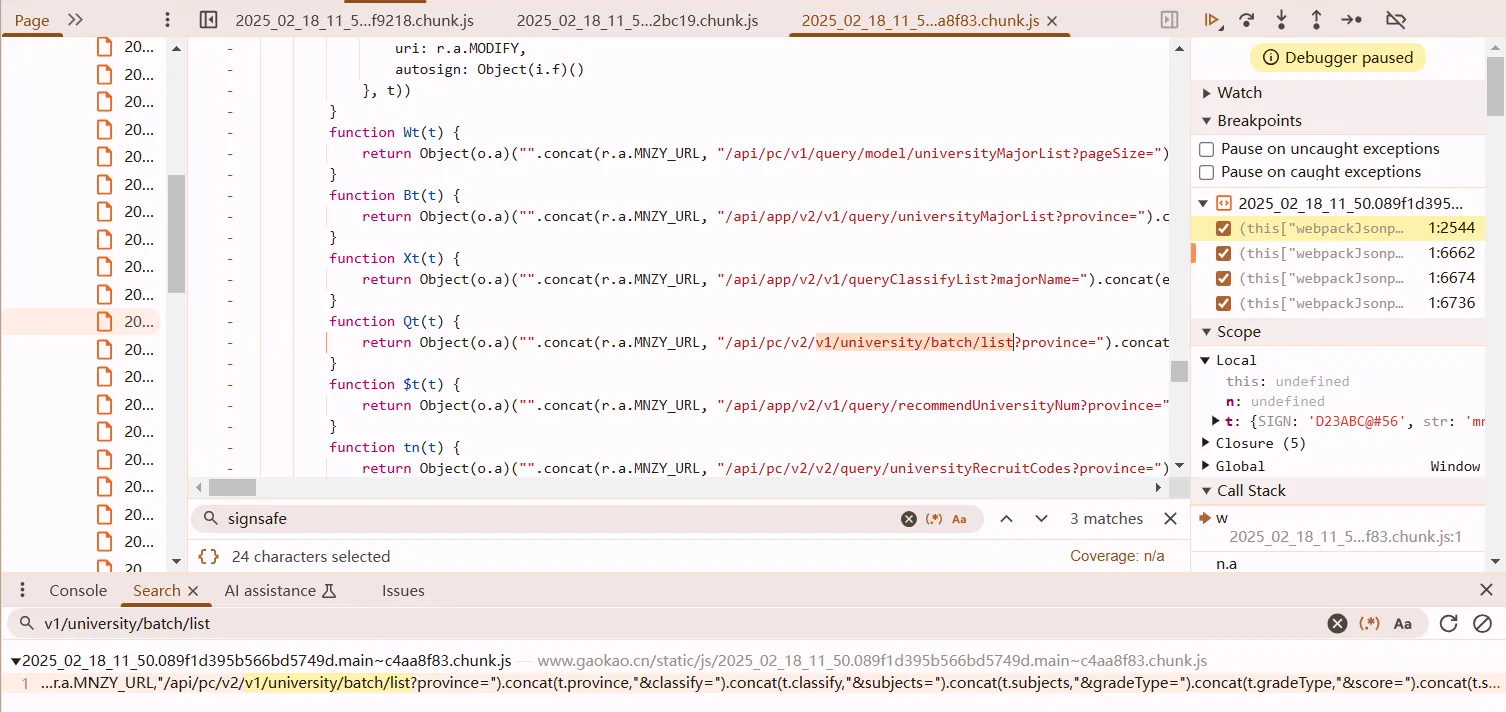
signsafe <- o <- w(),进入w,往上滑,是 5:
function w(t) {
var {SIGN: t, str: n} = t
, n = (n = decodeURI(n),
u.a.HmacSHA1(u.a.enc.Utf8.parse(n), t));
t = u.a.enc.Base64.stringify(n).toString();
return s()(t)
}
此文件拉到头上去,发现是webpack
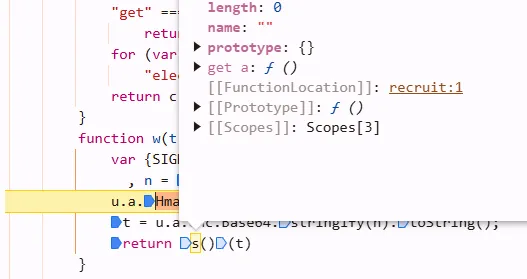
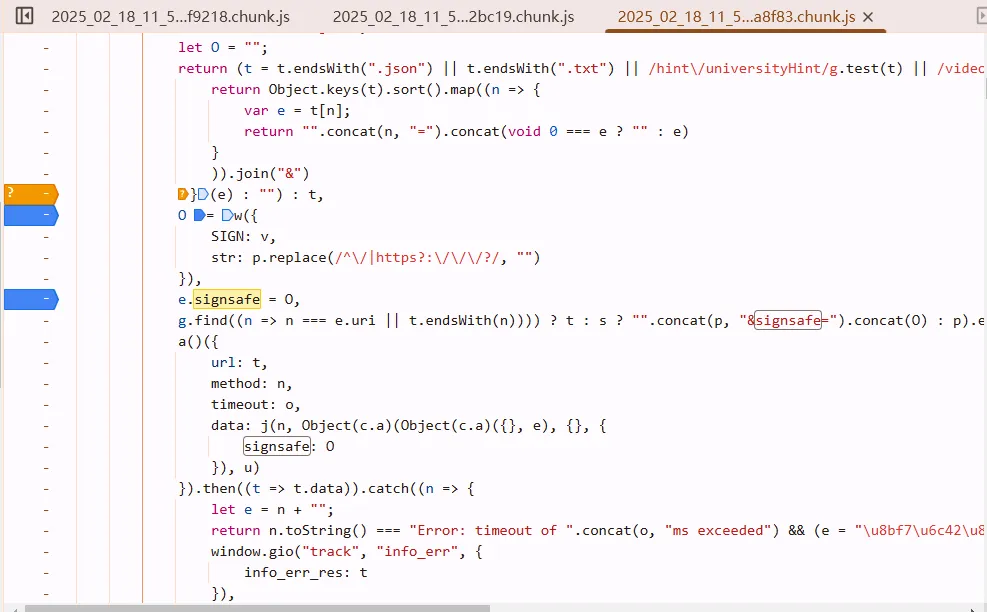
试图点进s,发现长这样。
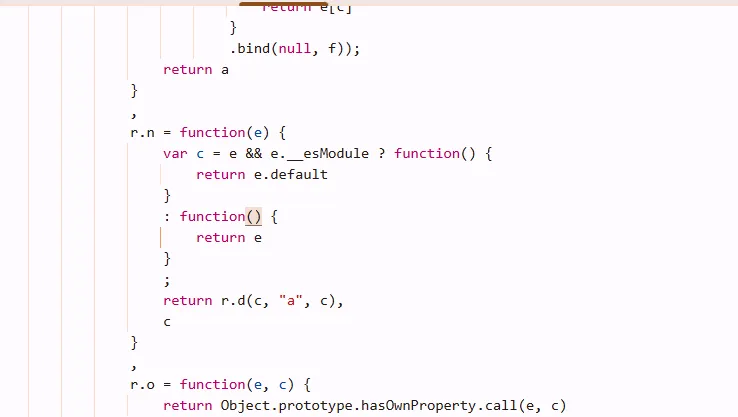
在console输入s()再点进去就能找到正确位置了
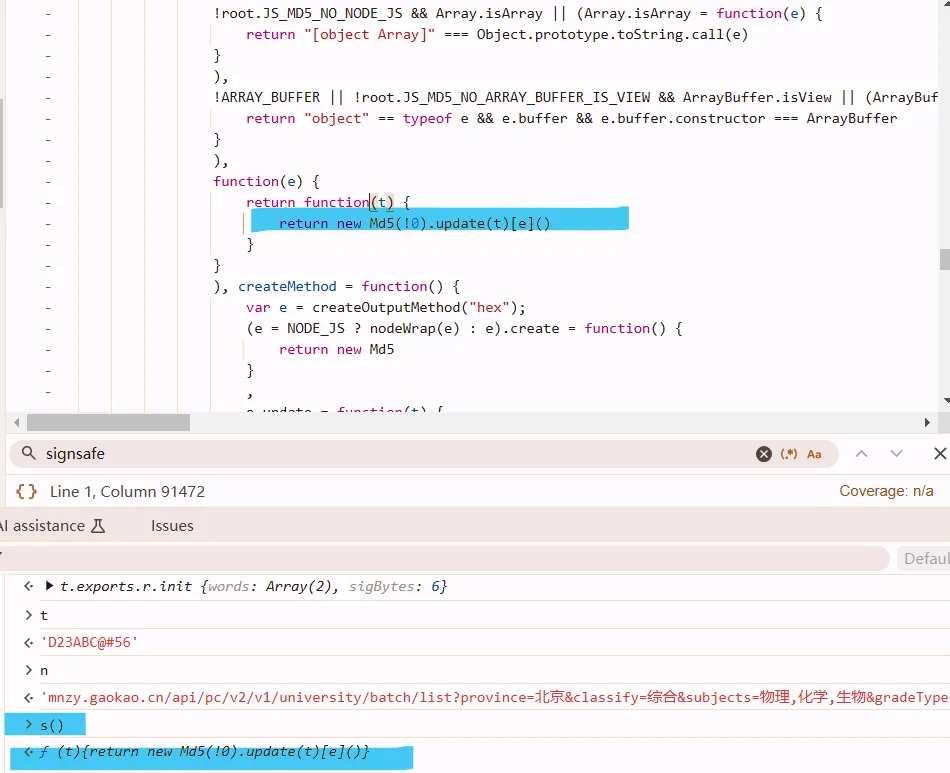
事已至此,可以直接写python还原了.作为sign的v是固定的
js2py
import hmac
import hashlib
import base64
import urllib.parse
def w(t):
sign = t
url_str = 'mnzy.gaokao.cn/api/pc/v2/v1/university/batch/list?province=北京&classify=综合&subjects=物理,化学,生物&gradeType=本科&score=495&zsgkId=263'
# Decode URI
decoded_str = urllib.parse.unquote(url_str)
print(decoded_str)
# Create HMAC-SHA1
hmac_obj = hmac.new(
sign.encode('utf-8'),
decoded_str.encode('utf-8'),
hashlib.sha1
)
# Get base64 of HMAC-SHA1
base64_str = base64.b64encode(hmac_obj.digest()).decode('utf-8')
print(base64_str)
# Apply MD5 to the base64 string
md5_hash = hashlib.md5(base64_str.encode('utf-8')).hexdigest()
return md5_hash
t = 'D23ABC@#56'
print(w(t))
